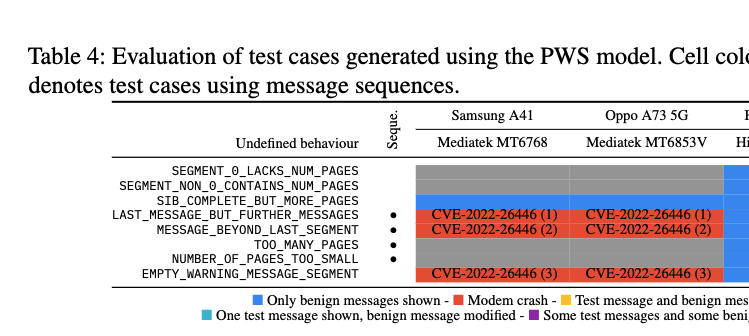
Instructions Unclear: Undefined Behaviour in Cellular Network Specifications
Daniel Klischies, Moritz Schloegel , Tobias Scharnowski , Mikhail Bogodukhov, David Rupprecht, and Veelasha Moonsamy
In this work, we present the first generic approach for systematically discovering undefined behaviour in cellular specifications. Requiring solely a model of the behaviour defined in the specification, our technique extends this model to automatically reason about the presence of undefined behaviour. For each undefined behaviour, it automatically infers concrete examples as proof of existence. This not only allows improving the specification but also enables us to test smartphone modems. This way, we can verify whether an instance of undefined behaviour leads to a security vulnerability within modem firmware. With our approach, we identify 58 cases of undefined behaviour in LTE's Public Warning System, SMS, and Radio Resource Control specifications. Five of these cases resulted in previously unknown vulnerabilities that allow adversaries to read modem memory contents and perform remote Denial of Service attacks (in one case just via a single SMS) against commonly used smartphone modems. So far, two CVEs of high and one CVE of critical severity have been assigned. to user plane traffic, potentially deterring network operators due to the increased workload. We studied the overhead from various integrity protection algorithms and their impact on device performance. Our findings shed light on performance differences on user end-devices and isolated algorithm performance. We aim to promote discussion on the benefits of user plane integrity protection and clarify misunderstandings about performance impacts for end-users.

Never Let Me Down Again: Bidding-Down Attacks and Mitigations in 5G and 4G
Bedran Karakoc, Nils Fürste, David Rupprecht, and Katharina Kohls
Bidding-down attacks compromise mobile network security by enabling weaker encryption algorithms or downgrades to older network generations, exposing users to multiple attack vectors. Despite known issues and mitigation efforts integrated into 4G and 5G specs, there's a lack of systematic identification and analysis of these attack vectors. We categorize and analyze a wide range of bidding-down attack vectors and mitigations, finding vulnerabilities in all attacks and devices, including 5G and recent flagship phones. We also demonstrate these exploits through case studies, highlighting a majority of systems as vulnerable. Our paper seeks to enhance bidding-down mitigations in specification and implementation.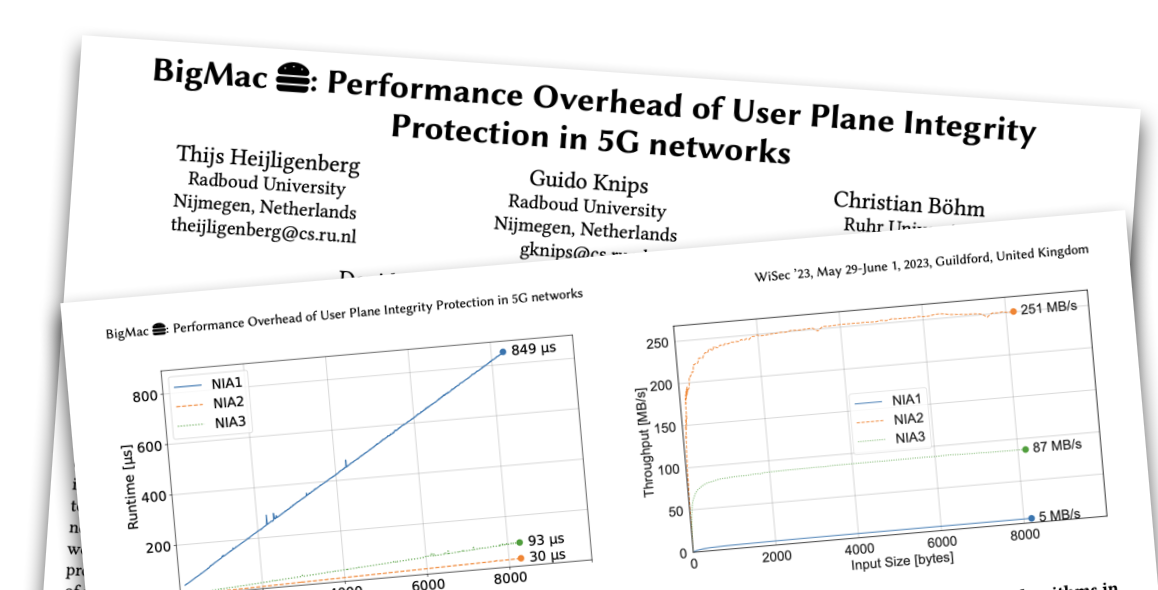
BigMac 🍔 Performance Overhead of User Plane Integrity Protection in 5G Networks
Thijs Heijligenberg, Guido Knips, Christian Böhm, David Rupprecht, and Katharina Kohls
5G's new security features address known issues in prior mobile generations, including integrity protection for user plane data that helps prevent manipulations such as DNS spoofing. However, this feature adds overhead to user plane traffic, potentially deterring network operators due to the increased workload. We studied the overhead from various integrity protection algorithms and their impact on device performance. Our findings shed light on performance differences on user end-devices and isolated algorithm performance. We aim to promote discussion on the benefits of user plane integrity protection and clarify misunderstandings about performance impacts for end-users.

Cryptanalysis of the GPRS Encryption Algorithms GEA-1 and GEA-2
Christof Beierle, Patrick Derbez, Gregor Leander, Gaëtan Leurent, Håvard Raddum, Yann Rotella, David Rupprecht, and Lukas Stennes
This study reveals the first public cryptanalytic attacks on the GEA-1 and GEA-2 algorithms, unveiling an intentional 40-bit security limit in GEA-1. The initial state of GEA-1 can be determined from a minimum of 65 bits of known keystream, requiring 240 GEA-1 evaluations and 44.5 GiB of memory. While GEA-2 lacks the same intentional weakness, it can be broken using algebraic methods and list merging algorithms in 245.1 GEA-2 evaluations, though 1600 bytes of keystream knowledge is needed. The identified weaknesses in GEA-1 and GEA-2 underscore an unusual, potentially purposeful, pattern limiting their security level.
5G SUCI-Catchers: Still Catching Them All?
Merlin Chlosta, David Rupprecht, Christina Pöpper, and Thorsten Holz
The paper introduces the 5G SUCI-Catcher attack, which demonstrates that despite advancements in 5G technology that encrypt user identifiers to protect their privacy, vulnerabilities still exist. The key contribution of the paper is the unveiling of an attack variant that allows the linking of encrypted identities across different sessions using the Authentication and Key Agreement (AKA) procedure. The paper further explores the attack's scalability, its practicality in real-world situations, and discusses potential countermeasures that network operators can employ. This advances our understanding of privacy limitations in 5G networks, paving the way for future solutions.
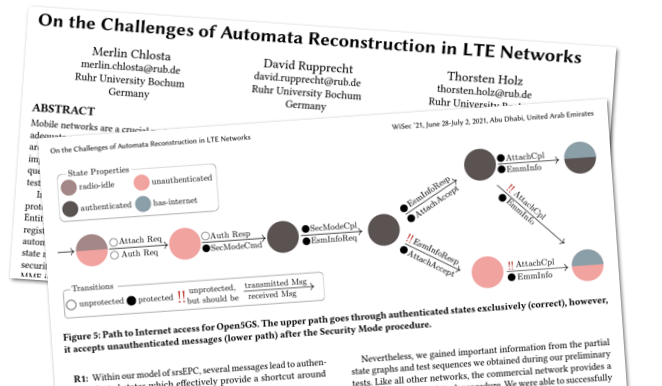
On the Challenges of Automata Reconstruction in LTE Networks
Merlin Chlosta, David Rupprecht, and Thorsten Holz
he 4G and 5G network standards are complex and challenging to implement, which led to several implementation issues being discovered over the last years. Consequently, we aim to strengthen automation in testing and increase test coverage to spot issues and potential security vulnerabilities. In this paper, we explore active automata learning for 4G/LTE protocol state machines. We focus on LTE's Mobility Management Entity (MME), the main core network element that handles all user registration and authentication through the NAS protocol. Based on automata learning, we automatically reconstruct the NAS protocol state machine to study implementation-specific artifacts and their security implications.This method allows testing of fully functional core networks without modification. Based on a prototype implementation, we test two open-source projects, one commercial MME implementation, and one MME in an operator's test network replicating the live LTE network. We expose several bugs, including crashes in three of the four implementations, potentially leading to network outages.

Call Me Maybe: Eavesdropping Encrypted LTE Calls With ReVoLTE
David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina Pöpper
Voice over LTE (VoLTE) is a packet-based telephony service seamlessly integrated into the Long Term Evolution (LTE) standard. By now all major telecommunication operators use VoLTE. To secure the phone calls, VoLTE encrypts the voice data between the phone and the network with a stream cipher. The stream cipher shall generate a unique keystream for each call to prevent the problem of keystream reuse. We introduce ReVoLTE, an attack that exploits an LTE implementation flaw to recover the contents of an encrypted VoLTE call. This enables an adversary to eavesdrop on VoLTE phone calls. ReVoLTE makes use of a predictable keystream reuse. Eventually, the keystream reuse allows an adversary to decrypt a recorded call with minimal resources.
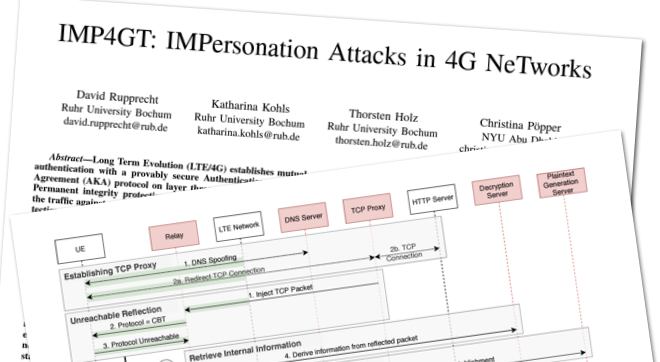
IMP4GT: IMPersonation Attacks in 4G NeTworks
David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina Pöpper
The IMP4GT (IMPersonation Attacks in 4G NeTworks) (/ˈɪmˌpæk(t)/) attacks exploit the missing integrity protection, and extend it with an attack mechanism on layer three which allows an attacker to impersonate a user towards the network and vice versa. We conduct two IMP4GT variants in a LTE commercial network and demonstrate how this completely breaks the mutual authentication of the user plane LTE and early 5G networks.

Breaking LTE on Layer Two
David Rupprecht, Katharina Kohls, Thorsten Holz, and Christina Pöpper
Voice over LTE (VoLTE) is a packet-based telephony service seamlessly integrated into the Long Term Evolution (LTE) standard. By now all major telecommunication operators use VoLTE. To secure the phone calls, VoLTE encrypts the voice data between the phone and the network with a stream cipher. The stream cipher shall generate a unique keystream for each call to prevent the problem of keystream reuse. We introduce ReVoLTE, an attack that exploits an LTE implementation flaw to recover the contents of an encrypted VoLTE call. This enables an adversary to eavesdrop on VoLTE phone calls. ReVoLTE makes use of a predictable keystream reuse. Eventually, the keystream reuse allows an adversary to decrypt a recorded call with minimal resources.